Consulting company PricewaterhouseCoopers The most recently announced lessons are lessons learned from the devastating and costly ransomware attack on Ireland’s public health system in May 2021. An unusually frank post-event investigation found that it was nearly two months after the initial intrusion to the launch of the ransomware.It also found that the affected hospitals had tens of thousands of obsolete Windows 7 System, and the IT administrators of the health system failed to respond to multiple warning signs that a large-scale attack was imminent.
PwC’s timeline before the deployment of Conti ransomware on May 14.
Irish Health Service Supervisor (HSE) Operating the country’s public health system has been hit Account ransomware May 14, 2021. The timeline in the report (above) stated that the initial infection of the “Patient Zero” workstation occurred on March 18, 2021, when an employee opened a Microsoft Excel file with a booby trap on a Windows computer. Phishing email sent a few days ago.
Less than a week later, the attacker established a reliable backdoor connection to the employee’s infected workstation. The report stated that after infecting the system, “the attacker continued to operate in the environment for eight weeks until the Conti ransomware detonated on May 14, 2021.”
according to PwC’s report (PDF), there are multiple warning signs about serious network intrusions, but these red flags are either misidentified or not acted fast enough:
- On March 31, 2021, HSE’s antivirus software detected the execution of two software tools commonly used by ransomware organizations—— Cobalt strike and Mimicac — On the zero patient workstation. But the antivirus software is set to monitor mode, so it does not prevent malicious commands. “
- On May 7, the attacker hacked into the HSE server for the first time. In the next five days, the intruder will hack into 6 HSE hospitals. On May 10, one of the hospitals detected malicious activity on its Microsoft Windows domain controller, which is a key “kingdom key” component of any Windows enterprise network that manages user authentication and network access.
- On May 10, 2021, the security auditor first discovered evidence of an attacker’s intrusion into the hospital C and hospital L systems. The antivirus software of Hospital C detected Cobalt Strike on both systems, but failed to isolate malicious files.
- On May 13, HSE’s anti-virus security provider sent an email to HSE’s security operations team, highlighting at least 16 unprocessed threat incidents on the system dating back to May 7. The HSE security operations team asked the server team to restart the server.
By the time it was too late. Just after midnight on May 14, Irish time, the attacker executed the Conti ransomware in the HSE.attack Services interrupted in several Irish hospitals It also led to the almost complete closure of HSE’s national and local networks, forcing many outpatient clinics and medical care services to be cancelled. Appointments in certain areas have fallen by 80%. “
Conti initially requested virtual currency worth 20 million U.S. dollars in exchange for a digital key to unlock the HSE server compromised by the organization. But perhaps in response to the public’s strong protest against the interruption of HSE, Conte changed direction and handed over the decryption key to HSE without payment.
Nevertheless, it will take months to restore the infected system. HSE eventually recruited members of the Irish army to bring laptops and personal computers to help manually restore the computer system. It was not until September 21, 2021 that HSE announced that 100% of its servers had been decrypted.
As bad as the HSE ransomware attack, the PwC report emphasizes that it could be worse. For example, since HSE’s backup infrastructure only regularly backs up to offline tapes, it is not clear how much data will be unrecoverable if the decryption key is not available.
The report found that the attack could also be worse:
- If the attacker intends to target specific equipment in the HSE environment (such as medical equipment);
- Whether the ransomware takes action to destroy data on a large scale;
- Whether the ransomware has automatic propagation and persistence functions, such as spreading to medical devices through the use of exploits across domains and trust boundaries (for example, the EternalBlue exploits used in WannaCry and NotPetya15 attacks);
- If the cloud system is also encrypted, such as the COVID-19 vaccination system
The PWC report contains many recommendations, most of which revolve around hiring new people to lead the organization’s double security efforts. But it is clear that HSE still has a lot of work to do in improving security maturity. For example, the report stated that more than 30,000 Windows 7 workstations in HSE’s hospital network were deemed discontinued by vendors.
“HSE assessed its cyber security maturity rating as low,” PwC wrote. “For example, they did not establish a CISO or security operations center.”
PricewaterhouseCoopers also estimated that efforts to establish HSE’s cybersecurity plan to the extent that it can quickly detect and respond to intrusions may cost “several times the HSE’s current capital and operating expenditures in these areas.”
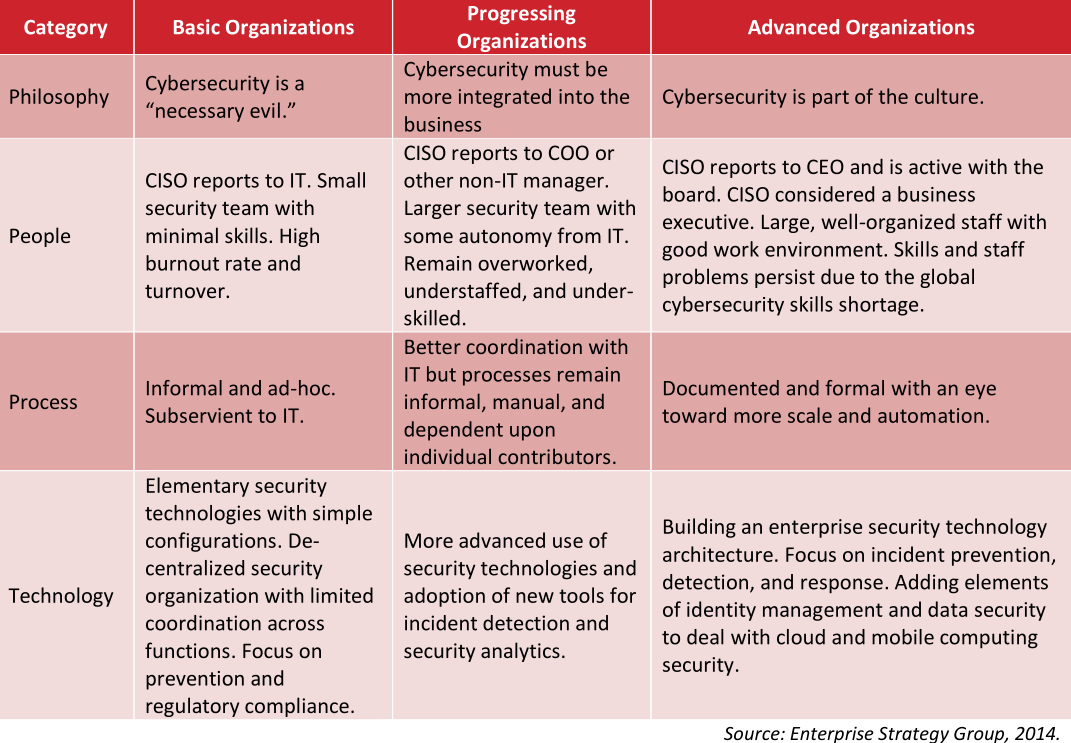
An idea of the “security maturity” model.
In June 2021, the HSE Director General stated that the cost of recovery from ransomware attacks in May May exceed $600 million.
The remarkable thing about this incident is that HSE is publicly funded by the Irish government, so theoretically, it has enough money to spend (or raise) all these ambitious proposals to improve its security maturity.
This is in stark contrast to the U.S. health care system, where the biggest obstacle to doing a good job in safety is still the lack of a real budget priority. In addition, most healthcare organizations in the United States are private companies with meager profits.
I know this because in 2018, I was asked to give a keynote speech at the annual conference Healthcare Information Sharing and Analysis Group (H-ISAC), an industry organization focused on sharing cyber security threat information. I hardly accepted the invitation: I hardly wrote an article on medical safety, which seems to be mainly reporting whether medical institutions have complied with the laws and regulations of the United States.This compliance focuses on Health Insurance Portability and Accountability Act (HIPPA), it gives priority to protecting the integrity and privacy of patient data.
To keep up with the progress, I interviewed more than a dozen of the best and brightest people in the medical security industry. A common perception I heard from interviewees is that if it is related to security but not to compliance, then it may not have a good chance of getting any budget.
These sources unanimously stated that no matter what kind of good intentions, it is unclear whether HIPPA’s “protecting data” regulatory approach is viewed from the perspective of overall threats.according to Medical informationTo date, more than 40 million patient records have been leaked in the incidents reported to the federal government in 2021 alone.
In my 2018 speech, I tried to emphasize the importance of being able to respond quickly to intrusions. This is part of what I told the H-ISAC audience:
“The term’security maturity’ refers to the street wisdom of an individual or organization. This maturity usually comes from making a lot of mistakes, being hacked a lot, and hoping to learn from each incident, measure the response time, and Improve.
Let me state in advance that all organizations will be hacked. If they are large enough, even people who do everything right from a security perspective can be hacked every day. Hacking refers to someone in the organization falling into a phishing scam, or clicking on a malicious link and downloading malicious software. Because let’s face it, hackers only need to mess up one to gain a foothold in the network.
Now this is not bad in itself. Unless you don’t have the ability to detect it and respond quickly. If you can’t do this, you run the serious risk of transferring a small incident to a bigger problem.
Think of it as a “golden time” medical concept: the short window of time after a traumatic injury such as a stroke or heart attack, in which case life-saving drugs and attention may be the most effective. The same concept applies to cybersecurity, which is why so many organizations now devote more resources to incident response, not just prevention. “
The somewhat fragmented health care system in the United States means that many ransomware outbreaks are often limited to regional or local health care institutions. However, a proper ransomware attack or a series of attacks can cause serious damage to the industry: A Deloitte report December 2020 Said that the top 10 health systems now control 24 market shares, and their revenue growth rate is twice that of other markets.
In October 2020, KrebsOnSecurity broke the news FBI and U.S. Department of Homeland Security I got gossip from a top ransomware organization that warned that “American hospitals and healthcare providers face an imminent threat of cybercrime.” Members associated with a Russian ransomware organization called Ryuk discussed plans to deploy ransomware in more than 400 medical institutions in the United States.
After running that article for a few hours, I started with a respected H-ISAC security expert who questioned whether it was worth making the public so angry. This story was updated several times throughout the day, and within 24 hours at least five medical institutions were attacked by ransomware.
“I think it would be helpful if I understand what the baseline is, such as how many medical institutions are attacked by ransomware in an average week?” I asked the source.
“It’s more like one a day,” the source revealed.
No matter how long it takes, HSE is very likely to obtain the funds needed to implement the plan recommended by PWC. I want to know how many American healthcare organizations would say the same thing.


