A previously unknown rootkit was discovered and set its sights on Hewlett-Packard Enterprise’s Integrated Lights-Out (Labor Organization) Server management technology to carry out brutal attacks, tampering with firmware modules and completely erasing data from the infected system.
Iranian cybersecurity company Amnpardaz documented the discovery this week, which is the first instance of real-world malware in iLO firmware.
“Many aspects of iLO make it an ideal utopia for malware and APT groups: extremely high privileges (above any access level in the operating system), extremely low-level access to hardware, completely out of sight of administrators, and security Tools, there is a general lack of knowledge and tools to check iLO and/or protect it, the persistence it provides for malware still exists even after changing the operating system, especially always running and never shutting down, “Researchers Say.
In addition to managing servers, iLO modules have extensive access to all firmware, hardware, software, and operating systems (OS) installed on the server. This fact makes them ideal candidates for disrupting organizations that use HP servers, while also enabling malware Be able to maintain persistence after restarting and continue to exist after reinstalling the operating system. However, the exact method of operation used to penetrate network infrastructure and deploy wipers is still unknown.
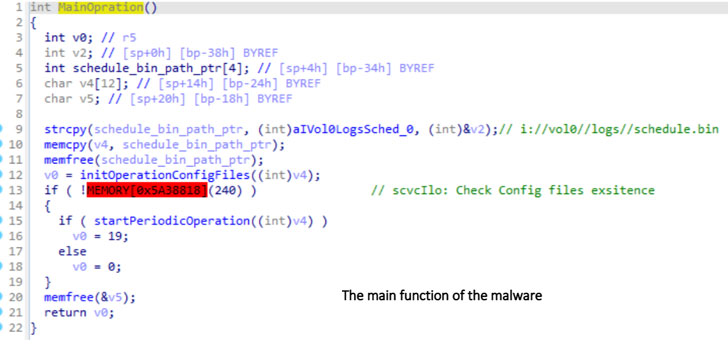
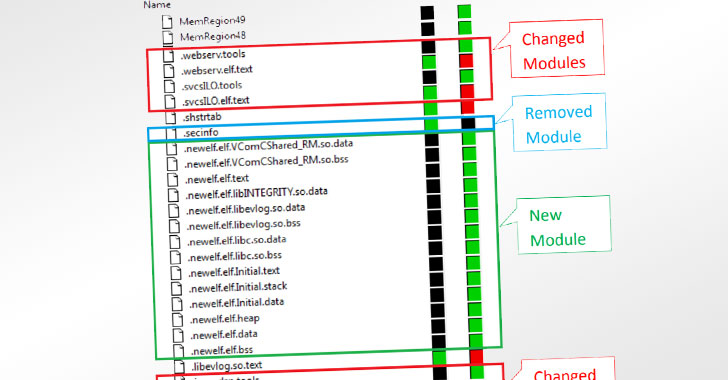
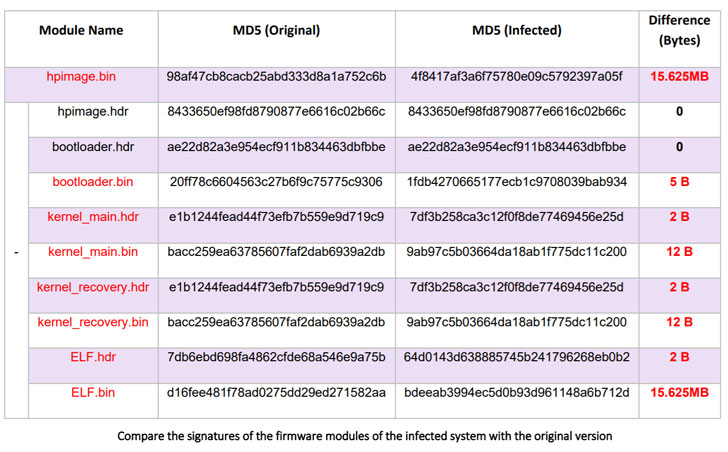
Dubbing bleedSince 2020, rootkits have been used in attacks to manipulate many original firmware modules to covertly prevent firmware updates. Specifically, the modifications made to the firmware routines simulate the firmware upgrade process-allegedly displaying the correct firmware version and adding related logs-without actually performing the update.
The researcher said: “This alone shows that the purpose of the malware is to become a rootkit with the greatest concealment and avoid all security checks.” “A type of malware that hides in one of the most powerful processing resources (always on ), can execute any command received from the attacker without being discovered.”
Although the identity of the adversary has not yet been determined, Amnpardaz describes rootkits as possibly the product of advanced persistent threats (APT), which refers to a nation-state or state-backed group that uses continuous, secret, and sophisticated hacking techniques to protect the future. Authorized to access the system and stay inside for a long time without attracting attention.
If so, development has made firmware security a priority again, requiring timely application of firmware updates provided by the manufacturer to reduce potential risks, separating the iLO network from the operating network, and regularly monitoring the firmware for signs of infection.
The researchers pointed out: “Another important point is that there are some ways to access and infect iLO through the network and the host operating system.” “This means that even if the iLO network cable is completely disconnected, there is still the possibility of malware infection. Interesting The thing is, there is no way to completely shut down or disable iLO when it’s not needed.”