Although law enforcement agencies have taken destructive actions against cybercrime groups to prevent them from becoming victims of other companies, ransomware organizations continue to improve their strategies and techniques to deploy file encryption malware on infected systems.
“Whether it’s due to law enforcement, group fighting, or people’s total abandonment of variants, RaaS [ransomware-as-a-service] The group that dominates the ecosystem at this point is completely different from a few months ago,” Intel 471 Researcher Say In a report released this month. “However, even if the variants have changed, the entire ransomware incident is still on the rise.”
Comprehensive enforcement actions carried out by government agencies in recent months have led to rapid changes in the RaaS landscape and reversed the situation of ransomware groups such as Avaddon, BlackMatter, Cl0p, DarkSide, Egregor, and REvil, forcing participants to slow down or shut down their businesses .
But just as these variants gradually became obscured, other budding groups have stepped in to fill the vacuum. The Intel 471 survey found that from July 2021 to September 2021, a total of 612 ransomware attacks can be attributed to 35 different ransomware variants.
Approximately 60% of observed infections are related to only four variants – led by LockBit 2.0 (33%), Conti (15.2%), BlackMatter (6.9%) and Hive (6%) – and mainly affect manufacturing Industry, consumer and industrial products, professional services and consulting, and the real estate industry.
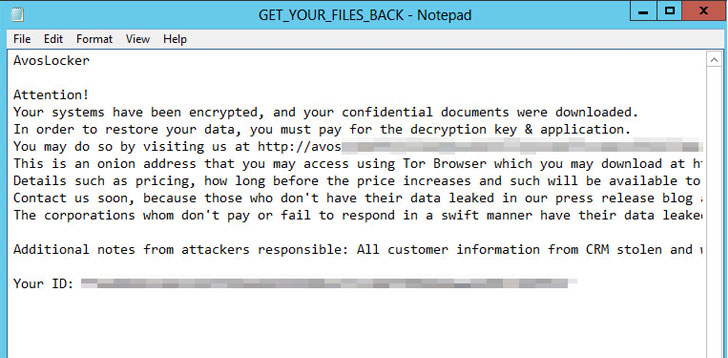
Avos locker It is one of many such cartels. These cartels have not only witnessed a surge in attacks, but also adopted new strategies to pursue their economic motives. The main one is the ability to disable endpoint security products on the target system and boot to Windows Safe to execute ransomware. The mode of the software. AnyDesk remote management tool is also installed to maintain access to the machine when running in safe mode.
“The reason for this is that many (if not most) endpoint security products do not run in safe mode-this is a special diagnostic configuration, Windows disables most third-party drivers and software, and may leave others protected Machines become insecure,” said Andrew Brandt, a security researcher in charge of SophosLabs, Say“The technology deployed by Avos Locker is simple and smart. The attacker ensures that the ransomware has the best chance to run in safe mode and allows the attacker to maintain remote access to the machine throughout the attack.”

Hive’s RaaS plan is called “radical” because it uses a pressure strategy to get victim organizations to pay the ransom, Group-IB Link Since its emergence in late June 2021, as of October 16, the attack pressure on 355 companies. At the same time, the Russian-language ransomware organization Everest is taking its ransomware strategy to a new level, threatening to sell access to the target system if they NCC Group say that their needs have not been met.
“Although the popularity of selling ransomware as a service has surged last year, this is a rare example of a group giving up ransom and providing access to IT infrastructure-but we may see imitation attacks and beyond in 2022 ,” the UK-based cybersecurity company Point out.
More importantly, a relatively new ransomware family called Pysa (aka Mespinoza) has replaced Conti as one of the top ransomware threat organizations along with LockBit 2.0 in November. Compared with October, the number of companies targeted by ransomware has increased by 50%, and attacks on government systems have surged by 400%.
“Although law enforcement agencies around the world have become more active in arresting the people behind the attacks, it’s still easy for developers to shut down popular variants, keep a low profile, and come back with fine-tuned malware used by themselves and their affiliates. “Intel 471 researchers said. “As long as developers can stay in the country where they are granted a safe harbor, the attack will continue, albeit in different variants.”





