
Adam Bannister December 1, 2021 15:32 UTC
Update time: December 1, 2021 16:06 UTC
Due to MSP supervision, the mail server is easily hijacked
The email authentication check could be deceived by phishing emails posing as nearly 200 Australian organizations because the vulnerability was discovered more than two years after it was conceived.
It has now been fixed and the problem has been traced to the hosting service provider (MSP) who designed the organization’s website and managed its domain name server (DNS) and email infrastructure.
CanIPhish CEO and Palo Alto Networks cloud security architect Sebastian Salla said that the MSP Precedence Group in question “unfortunately added an extremely over-permissive SPF DNS record to each domain.” Drink it every day.
Don’t forget to read HTML smuggling: New attack techniques are increasingly used to target the banking industry
“Because MSP [had] By adding each AWS address block in Australia to the SPF record of each organization, any Amazon Web Services (AWS) user can start virtual machines and send authenticated emails as if they came from these organizations,” Salla Say Drink it every day.
According to a Blog post Salla was released today (December 1st). Attackers only need to obtain any one of many SPF-compliant IP addresses that are not controlled by the target organization to pass SPF and DMARC authentication checks.
“You can combine these address blocks with AWS public IP range file Seeing this problem,” Sara added.
What is SPF?
this Sender Policy Framework (SPF) is an email authentication mechanism designed to detect fraudulent emails sent on the surface on behalf of legitimate entities.
The organization specifies a list of IP addresses that are authorized to send emails on their behalf in their SPF record, which is published on their DNS.
Therefore, emails purporting to be from an organization and originating from an IP address not listed in its SPF record will be marked as suspicious.
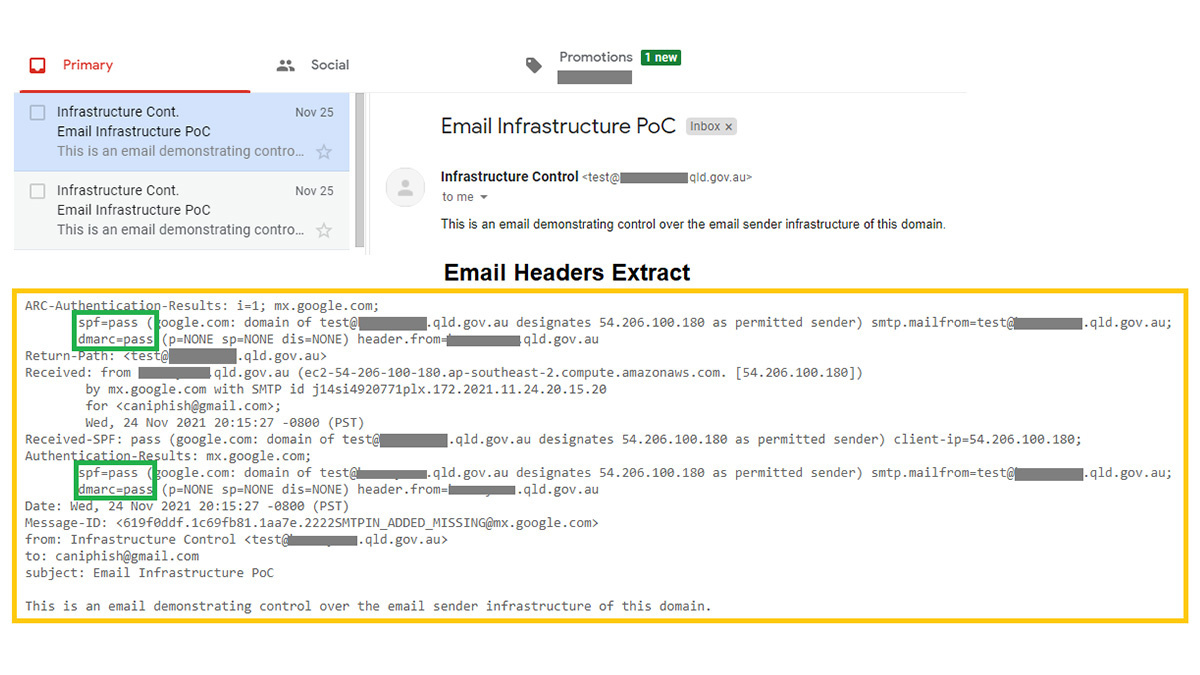 Sara sent herself an email claiming to be from the city council, which passed the email verification
Sara sent herself an email claiming to be from the city council, which passed the email verification
‘Extreme risk’
Salla found that 190 organizations were affected by MSP SPF supervision, including city councils, financial services companies, freight services companies, law firms, and construction companies.
“Given the location of many of these organizations (ie in and around property/financial services), Australian individuals face extreme risks in the form of commercial email intrusion attacks,” Salla said.
“Threat actors who stumble upon any of these organizations can find customers and send fake invoices, purchase orders, etc., and they are absolutely unable to distinguish between true and false.”
Learn about the latest email security news
Salla’s discovery began with a “one-time scan of hundreds of Australian organizations” showing the city council a bunch of address blocks in its SPF records, which are in contrast to “each IP address reserved by AWS for EC2 instances in Australia- 1,048,544 IP addresses overlapped “”.
He verified his suspicion by creating an EC2 instance with an authorized IP address and sending himself an email pretending to be the council to bypass SPF and DMARC checks.
Salla discovered that MSP’s SPF record has been in its vulnerable form since March 2019.
repair
According to Salla, the Precedence Group resolved the issue on Monday (November 29)-on the same day, the Australian Cyber Security Centre issued an alert to it, and the researchers notified the issue on November 25.
Salla stated that MSP has “removed all overly loose address blocks and replaced them with the individual IP addresses of the mail servers actually under its control” — thus “immediately applying the fix to all affected customers”.
Salla’s research in this area is ongoing. “In the next few weeks/months, I fully hope that as I begin to expand the scope of these scans and improve the methods, more organizations will be discovered,” he explained.
Precedence Group did not respond to our request for comment. If we receive a response, this article will be updated.
You might also like Panasonic admits to data breach after attacker gained access to file server


