Security company Kaspersky stated in a December 16 briefing that an organization with similar strategies, technologies, and procedures to the North Korean Lazarus Group has targeted government and privacy industry computers until 2021, with a focus on Industrial Control System (ICS).
As of November 10, the unaffiliated organization has installed a malware called PseudoManuscrypt by Kaspersky on more than 35,000 systems in 195 countries/regions because its function is similar to the Manuscrypt program used by Lazarus Group. Although the operation did not seem to single out any industry, the affected systems included computers in military industrial enterprises and research laboratories, and more than 7% of the computers were installed as part of industrial control systems.
Kaspersky security expert Vyacheslav Kopeytsev said that although the attack was not noticeable because of the number of infected systems, the number of sensitive systems should attract people’s attention.
“The fact that there are a large number of ICS computers around the world—thousands of them based on our telemetry data alone, and possibly more—were attacked during this event, which undoubtedly makes it a threat that deserves close attention. . Experts responsible for the safety and security of the workshop system and its continuous operation,” he said.
“As a large number of engineering computers are under attack, including systems for 3D and physical modeling,” he added, “the development and use of digital twins raises the issue of industrial espionage as one of the possible targets of this campaign.”
For defenders, industrial control systems are highly risky due to their vulnerability and the potential impact of attacks. Many of these systems are relatively old and predate the increasing attention to security design and development in the past decade, leaving features that are essentially design loopholes that can be easily manipulated by attackers. The hijacking of the Ozma Water Treatment Plant in Florida in early 2021 highlighted the possibility of simple attacks on unsafely designed infrastructure.
However, malware attacks, such as PseudoManuscrypt, are still a common way to cross between IT networks and OT networks. The malware was first installed through counterfeit and pirated software (including ICS software) and a malware-as-a-service (MaaS) network. Kaspersky AnalyticsAfter a complex installation chain, the malware collects information from the linked computers and devices.
“The most serious impact of this malware is the theft of confidential data-login names and passwords, VPN connection settings, screenshots, and even video recordings on the screen; all of these are collected by PseudoManuscrypt,” Kopeytsev said.
The connection with the Lazarus group is quite weak.The business of the Lazarus Group is related to the North Korean Government Reconnaissance Bureau, and its activities Overlaps with APT37, APT38 and KimsukyIn an operation called ThreatNeedle, the Lazarus Group used a custom malware called Manuscrypt, which has many similarities with the new malware PseudoManuscrypt. Additional information issued by Kaspersky.
Kopeytsev said: “Both malicious programs load payloads from the system registry and decrypt them.” “The executable files of the two malicious programs have almost the same export table. In addition, the two malicious programs use similar Perform file naming format.”
Other clues to the attacker’s identity include Chinese annotations in program metadata, the use of libraries previously used by the Chinese state-sponsored organization APT41, and communications with command and control servers sent in Chinese.
“[W]Kaspersky stated in its analysis that we are unable to determine whether the activity was a mercenary goal for criminal pursuits or a goal related to the interests of certain governments. “However, the fact that the system being attacked includes computers from well-known organizations in different countries allows us to assess the threat level as high.”
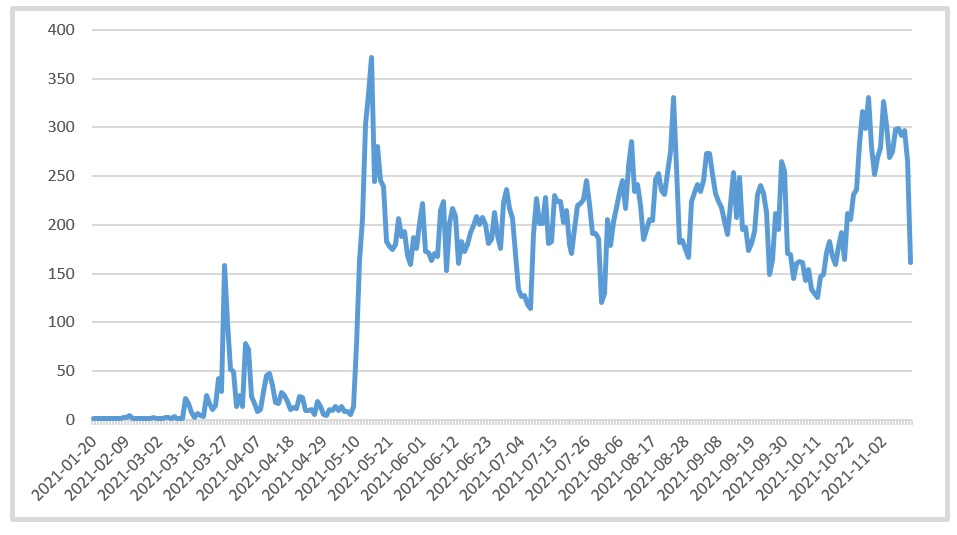
In the first four months of 2021, the company only detected a low level of PseudoManuscrypt detection, but that changed in May, detecting more than 200 instances of malware every day. The countries most affected by continued attacks are Russia, India, and Brazil, which account for more than 30% of all computers attacked with PseudoManuscrypt. American organizations are the eighth largest goal, accounting for only 2.4% of activities.
Of the industrial systems that were attacked, 44% were in the engineering and building automation industries.
Some common-sense steps can help companies deal with malware, even malware targeting ICS. The overall security can be improved by requiring an administrative password to turn off security, and two-factor authentication can prevent credential stuffing attacks. Kaspersky said that manufacturers, engineering companies and utility companies should use special security measures to protect their workshop systems.