Network security researchers demonstrated a new attack technique that can use the Bluetooth component of the device to directly extract the network password and manipulate the traffic on the Wi-Fi chip.
This novel attack is aimed at so-called “combined chips”, which are chips specifically designed to handle different types of wireless communications based on radio waves, such as Wi-Fi, Bluetooth, and LTE.
“The empirical evidence we provide shows that coexistence, that is, the coordination of cross-technology wireless transmission, is an untapped attack surface,” a team of researchers from Darmstadt University of Technology’s Secure Mobile Networking Laboratory and the University of Brescia wrote in a report. The report said. New article.
“Instead of directly upgrading to the phone [operating system], Wireless chips can use the same mechanism they use to arbitrate access to shared resources to upgrade their privileges to other wireless chips, namely the transmitting antenna and the wireless medium. “
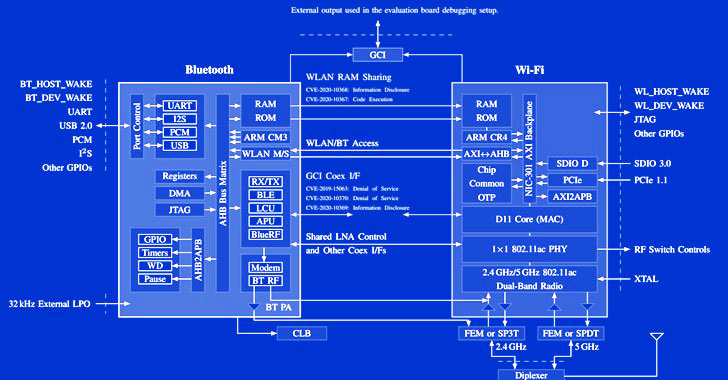
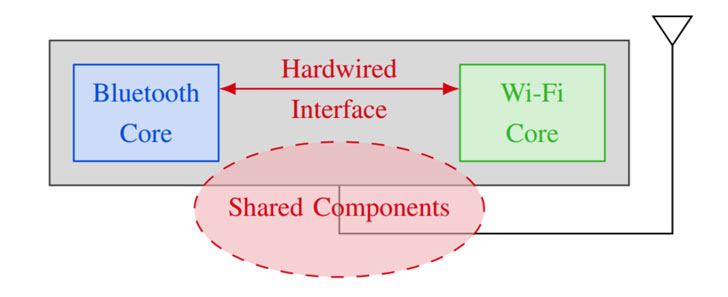
coexist Refers to a mechanism in which Bluetooth, Wi-Fi, and LTE share the same components and resources (such as antennas or wireless spectrum), so these communication standards must coordinate spectrum access to avoid conflicts when operating on the same frequency. Chipset vendors use this principle to allow Wi-Fi and Bluetooth to operate almost simultaneously.
Although these combined wireless chips are the key to high-performance spectrum sharing, as the same group of researchers has proved, coexisting interfaces can also bring side-channel risks. Black Hat Security Conference Last year, it effectively allowed malicious parties to gather detailed information from other wireless technologies supported by the combo chip.
The vulnerability class called “Spectra” is based on the fact that the transmission occurs in the same frequency spectrum and the wireless chip needs to arbitrate channel access. This breaks the separation between Wi-Fi and Bluetooth, resulting in spectrum access denial of service, information leakage, and even a horizontal authority increase from the Bluetooth chip to the code execution on the Wi-Fi chip.
“The Wi-Fi chip encrypts network traffic and saves current Wi-Fi credentials, thereby providing attackers with more information,” the researchers said. “In addition, an attacker can execute code on the Wi-Fi chip even if it is not connected to the wireless network.”
In addition, the researchers found that it is possible for an attacker controlling the Wi-Fi core to observe Bluetooth data packets, which in turn can determine the time of keystrokes on the Bluetooth keyboard, ultimately enabling the attacker to reconstruct the text entered using Bluetooth. keyboard.
Although some attack scenarios were reported to vendors as early as August 2019, so far, the coexistence flaws on Broadcom SoC have not been patched.
Scholars said: “As of November 2021, more than two years after the first coexistence vulnerability was reported, coexistence attacks, including code execution, still apply to the latest Broadcom chips.” “This highlights how these problems are in practice. How difficult to solve.”
To minimize the risk of such wireless attacks, it is recommended that users remove unnecessary Bluetooth pairings, delete unused Wi-Fi networks, and restrict the use of cellular networks instead of Wi-Fi in public places.
The researchers concluded: “In recent years, cellular data plans have become more affordable, and cellular network coverage has increased.” “Wi-Fi is disabled by default and enabled only when using trusted networks can be considered a very Good security practice, even if it is troublesome.”