Since July 2020, a complex and well-equipped cyber espionage organization has launched a continuous campaign, and the transportation industry and government agencies related to the industry have become victims. This seems to be another increase in malicious activities on the tip of the iceberg.
“The organization tried to access some internal files (such as flight schedules and financial planning files) and personal information of the infected host (such as search history),” Trend Micro researchers Nick Dai, Ted Lee and Vickie Su Say In a report published last week.
Centaur of the Earth, also known as the nickname Pirate Panda And Tropic Trooper, a long-standing threat organization focusing on information theft and espionage activities. Since 2011, it has been launching targeted activities in Taiwan, the Philippines and Hong Kong against the government, healthcare, transportation, and high-tech industries. .
The hostile agent is believed to be a Chinese-speaking actor known for using spear-phishing emails with weaponized attachments to exploit known vulnerabilities, while advancing its malicious tools with confusion, concealment and surprising power.
“This threat group is proficient Red teamwork,” the researcher elaborated. “The organization knows how to bypass security settings and keep its operations unhindered. The use of open source frameworks also enables the organization to effectively develop new backdoor variants. “
In May 2020, the operator is Observed By deploying a USB Trojan called USBFerry to attack physically isolated networks belonging to Taiwanese and Philippine government agencies and military entities to steal sensitive data through removable flash drives, they can fine-tune their attack strategies with new behaviors.
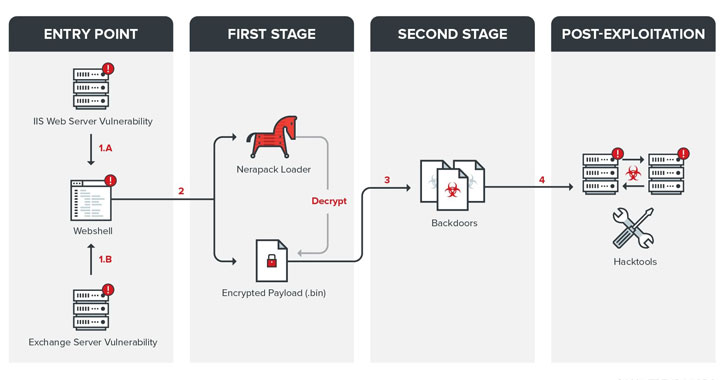
The latest multi-stage intrusion sequence detailed by Trend Micro involves the organization turning to use vulnerable Internet Information Services (IIS) servers and Exchange server vulnerabilities as entry points to install a web shell, and then use the web shell to provide .NET-based Nerapack loading The program and the first stage backdoor are called Quasar On the infected system.
From there, the attacker dropped the second-stage implants (such as ChiserClient, SmileSvr, ChiserClient, HTShell, and customized versions of Lilith RAT and Gh0st RAT, depending on the victim to retrieve further instructions from the remote server, download additional payloads, and execute File operations, execute arbitrary commands, and send the results back to the server.
It did not end there. After successfully exploiting the system, Tropic Trooper also tried to use a set of specific tools to disrupt the intranet, dump credentials and clear the event log on the infected machine. A command-line program called Rclone was also used, which enabled participants to copy the collected data to different cloud storage providers.
“At present, we have not found any substantial damage caused by threat organizations to these victims,” Trend Micro analysts explained. “However, we believe it will continue to collect internal information from infected victims. It is just waiting for the opportunity to use this data.”
These findings are worth noting because of the steps taken by Advanced Persistent Threats (APT) to avoid detection and the key nature of the target entity, not to mention the new features developed for its malware that can stay on the infected host and avoid detection.
“The organization can map the target’s network infrastructure and bypass the firewall,” the researchers said. “It uses backdoors with different protocols and deploys them according to the victims. It also has the ability to develop custom tools to evade security surveillance in different environments. It uses vulnerable websites and uses them as [command-and-control] server. “