Cybercriminal groups deploying ransomware rarely gain initial access to their targets on their own. More commonly, this access is purchased from a cybercrime broker who specializes in obtaining remote access credentials (such as the username and password required to remotely connect to the target network). In this article, we will look at “my father,” the handle chosen by cybercriminals, who has repeatedly sold such access rights to ransomware groups in the past few years.
Since the beginning of 2020, Babam has set up multiple auctions on Russian cybercrime forums Development, Which mainly sells virtual private network (VPN) credentials stolen from various companies. Since joining Exploit in 2015, Babam has written more than 270 posts, including dozens of sales topics. However, none of Babam’s Exploit posts contained any personal information or clues about his identity.
But in February 2016, Babam joined Verified, Another Russian crime forum. Verified has been hacked at least twice in the past five years, and its user database has been posted online. This message shows that Babam has added “verification” using an email addressOperator@gmail.com. The latest Verified leak also exposed private messages between forum members, including more than 800 private messages sent or received by Babam on the forum over the years.
In early 2017, Babam revealed to another verified user via private message that he was from Lithuania. In almost all of his forum posts and private messages, you can see that Babam uses transliteration of Russian instead of Cyrillic to communicate. This is very common among cybercriminals whose native language is not Russian.
Network Intelligence Platform Constellation Intelligence Tell KrebsOnSecurity that the operns@gmail.com address was used in 2016 Movie input, This is a movie streaming service for Lithuanian speakers. The username associated with this account is “bo3dom. “
Reverse WHOIS search passed Domain Tool.com Say operans@gmail.com is used to register two domain names: Bonnjoeder[.]Back in 2011, there are sanjulianhotels[.]com (2017). It’s unclear whether these domain names were ever online, but the street addresses on both records are “24 Brand Street“in England. [Full disclosure: DomainTools is a frequent advertiser on this website.]
A reverse search for “24 Brondeg St.” on DomainTools revealed another domain: World Wide Web[.]withThe use of domains starting with “www” is quite common among phishers, and when people enter the domain by mistake, passive “cybersquatting” websites will try to steal credentials from legitimate websites, such as accidentally missing ” .”. After entering “www”.

The banner on the homepage of the Russian cybercrime forum is verified.
Search for the phone number in the WHOIS record of wwwecardone in the domain tool[.]com — +44.0774829141 — led to some similar cybersquatting, including wwwebuygold[.]with with Alipay[.]with. wwwebuygold Different UK phone numbers from recent records[.]com domain — 44.0472882112 — is associated with two other domains — How to unlock iphonefree[.]with, with Alipay[.]with. All these domain names can be traced back between 2012 and 2013.
The original registration records of iPhone, Sagepay, and Gold domains share an email address: devrian26@gmail.com. Use the service of Constella to search for the username “bo3dom” and you will find an account located at ipmart-forum.com, A non-existent forum focusing on IT products such as mobile devices, computers, and online games.The search shows the email address registered by the user bo3dom on ipmart-forum.com devrian27@gmail.com, And the Internet address from Vilnius, Lithuania.
Devrian27@gmail.com is used to register multiple domains, including wwwsuperchange.ru Back in 2008 (note again the suspicious “www” as part of the domain name). The password recovery function of Gmail says that the backup email address of devrian27@gmail.com is bo3*******@gmail.com. Gmail accepts the address bo3domster@gmail.com As the recovery email for the devrian27 account.
According to Constella, the bo3domster@gmail.com address has been exposed in multiple data breaches over the years, and in each case it uses one of two passwords: “lebeda1” with”a123456“.
Searching for accounts with these passwords in Constella will reveal a large number of additional “bo3dom” email addresses, including bo3dom@gmail.com. The person whose name is displayed centered on the address in Constella Vitaus Mokus Use it to register an account on mindjolt.com, the site provides dozens of simple puzzle games, visitors can play these games online.
At some point, mindjolt.com was apparently also hacked, because its database copy in Constella said that bo3dom@gmail.com used two passwords on the site: lebeda1 with a123456.
Reverse WHOIS search for “Vytautas Mockus” on DomainTools shows email address devrian25@gmail.com Used to register domain names in 2010 Perfect currency[.]cooperate. This is a character Perfect currency[.]with, This is an early virtual currency, which was very popular with cybercriminals at that time. The phone number associated with the domain name registration is “86.7273687“.
Searching for “Vytautas Mockus” on Google will find that there is a person by this name who runs a mobile food service company in Lithuania named “Palvisa. ”A report on Palvisa (PDF) purchased from Necessities.ex — Official online directory of Lithuanian companies — said Palvisa was created by Vytautaus Mockus in 2011 using phone numbers 86.7273687, And the email address bo3dom@gmail.com. The report pointed out that Palvisa is very active, but has no employees other than the founder.
Through the bo3dom@gmail.com address, the 36-year-old Mr. Mockus expressed confusion about how his personal information appeared in so many records. “I was not involved in any crimes,” Morcus wrote in response.
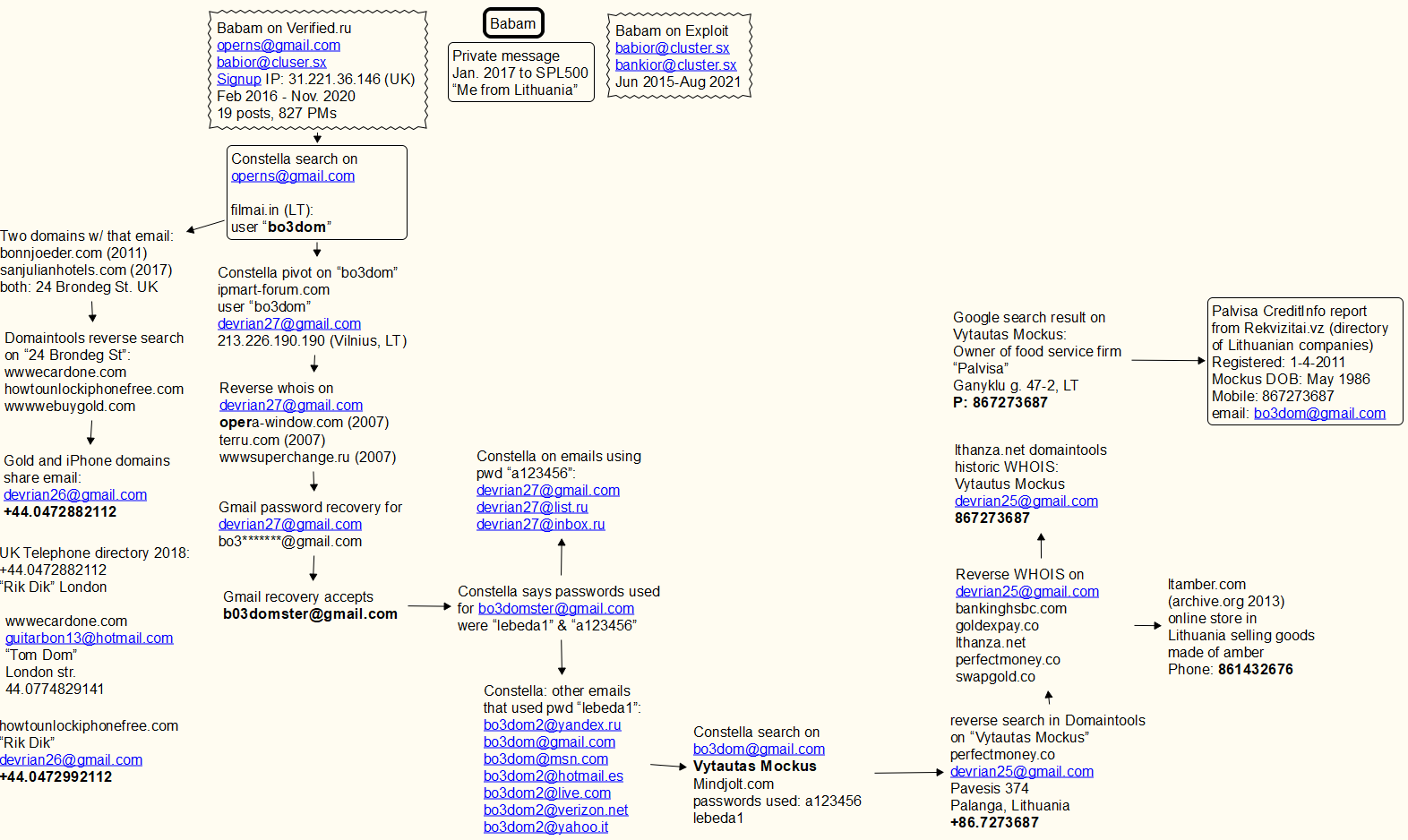
A rough mind map of the connections mentioned in this story.
The apparently registered domain names of Babam in the past 10 years indicate that he has begun to steal information mainly from other online scammers. By 2015, Babam aggressively “swiped cards”, that is, selling and using stolen payment card data. By 2020, he will almost completely shift his attention to the access rights of the sales company.
Introduction made by threat intelligence companies Flash point Said that Babam has received at least four positive feedback comments on the use of cybercrime forums. These comments came from LockBit Ransomware Gang.
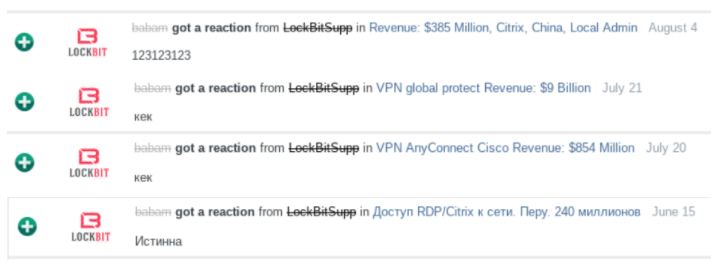
The ransomware collective LockBit provided positive feedback to Babam to sell access to different victim organizations.Picture: Flash point
According to Flashpoint, in April 2021, Babam sold a Citrix certificate for an international company active in the field of laboratory testing, inspection, and certification, with annual revenue of more than US$5 billion and more than 78,000 employees.
Flashpoint said that Babam initially announced that he had sold access rights, but then reopened the auction as potential buyers withdrew from the transaction. A few days later, Babam reposted the auction, adding more information about the depth of illegal access and lowering his asking price. The access was sold in less than 24 hours.
“Based on the statistics provided and reports from sensitive sources, Flashpoint analysts are very confident in assessing that the infected organization is likely Bureau Veritas International Inspection Group, An organization headquartered in France, doing business in various fields,” the company concluded.
In November last year, Bureau Veritas admitted that it Shut down its network in response to cyber attacksThe company has not yet stated whether the incident involved ransomware and what type of ransomware if it was involved, but the company’s response to the incident came directly from the script for responding to ransomware attacks. Bureau Veritas has not yet responded to a request for comment; its Latest public statement on December 2 No other details about the cause of the incident were provided.
Flashpoint pointed out that Babam has been using transliteration of Russian in Exploit and Verified until around March 2020, when he switched to Cyrillc in forum comments and sales leads. Flashpoint stated that this may indicate that another person has started to use a Babam account since then, or, more likely, that Babam had only a small grasp of Russian at the beginning, and his language skills and confidence gained over time. improve.
Flashpoint found that the credibility of the latter theory is that Babam still has language errors in his posts, implying that Russian is not his original language.
“Threat actors using double “n” in words such as “проданно” (correct-продано) and “сделанны” (correct-сделаны) prove that this style of writing is impossible when using machine translation, because it will not It’s the correct spelling of the word,” the Flashpoint analyst wrote.
“These types of grammatical errors often occur among people who have not received enough education in school or whose second language is Russian,” the analysis continued. “In this case, when someone tries to spell a word correctly, they accidentally or unknowingly misspelled it and made these types of mistakes. At the same time, the spoken language can be fluent or even native. For people from the former Soviet Union For people in the country, this is usually typical.”


