Cybersecurity researchers have detailed a critical flaw in the KCodes NetUSB component integrated into millions of end-user router devices from Netgear, TP-Link, Tenda, EDiMAX, D-Link, and Western Digital, among others.
code network usb is a Linux kernel module that enables devices on the local network to provide USB-based services over IP. Printers, external hard drives, and flash drives that plug into Linux-based embedded systems (eg, routers) are available over the network using drivers.
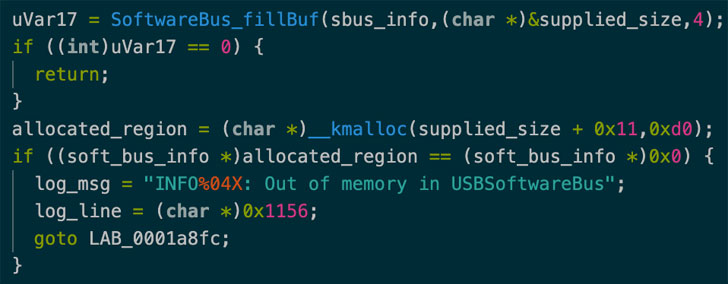
CVE-2021-45608 (CVSS score: 9.8), since the security breach is tracked as, with buffer overflow vulnerability If successfully exploited, attackers can remotely execute code in the kernel and perform malicious activities of their choice. Report SentinelOne shared with Hacker News.
This is the latest in a series of NetUSB vulnerabilities patched in recent years. In May 2015, researchers at SEC Consult disclosed another buffer overflow vulnerability (CVE-2015-3036) that could lead to a Denial of Service (DoS) or code execution.
Then in June 2019, Cisco Talos leaked Details of two vulnerabilities in NetUSB (CVE-2019-5016 and CVE-2019-5017) that could allow an attacker to inappropriately force selected Netgear wireless routers to disclose sensitive information or even enable remote code execution .
After responsibly disclosed to KCodes on September 20, 2021, the Taiwanese company released a patch to all vendors on November 19, after which Netgear release Firmware update containing bug fixes.
SentinelOne has avoided releasing proof-of-concept (PoC) code given that other vendors are still in the process of releasing updates. But the cybersecurity firm warned that despite the technical sophistication involved, vulnerabilities could still emerge in the wild, so users must apply fixes to mitigate any potential risks.
“Because this vulnerability resides in third-party components licensed to various router vendors, the only way to address this issue is to update the router’s firmware, if one is available,” said researcher Max Van Amerongen. “Check your router for Not an end-of-life model is important as it is unlikely to receive an update for this vulnerability.”





