Operators linked to Lazarus subgroup BlueNoroff have been linked to a series of cyberattacks against small and medium-sized companies around the world aimed at draining their cryptocurrency funds, another prolific North Korean state-sponsored financially motivated action actor .
Russian cybersecurity firm Kaspersky is tracking cybersecuritysnatch cryptocurrency” noted that the campaign has been running since 2017, adding that the attacks targeted fintech startups located in China, Hong Kong, India, Poland, Russia, Singapore, Slovenia, Czech Republic, UAE, US, Ukraine and Vietnam.
“Attackers have been subtly abusing the trust of employees working at target companies, sending them a full-featured Windows backdoor with surveillance capabilities, disguised as contracts or other business documents,” the researchers said. Say. “To finally empty the victim’s crypto wallet, the attackers developed extensive and dangerous resources: sophisticated infrastructure, exploits, and malware implants.”
BlueNoroff and larger Lazarus umbrellas are A known Deploy a diverse malware arsenal and conduct multi-pronged attacks on businesses to illicitly obtain funds, including relying on advanced phishing tactics and sophisticated malware to finance the sanctioned North Korean regime and its nuclear weapons and Ballistic Missile Revenue Creation Missile Program.
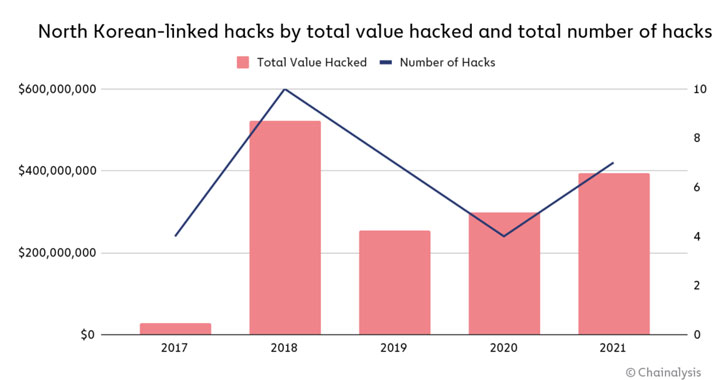
If anything, these cyber offensives are paying off hugely.according to a new report The Lazarus Group, published by blockchain analytics firm Chainalysis, has been linked to seven attacks on cryptocurrency platforms that have withdrawn nearly $400 million worth of digital assets in 2021 alone, up from $300 million in 2020.
“These attacks are mainly targeting investment firms and centralized exchanges […] Draw money from the internet connections of these organisations “Hot” wallet “Once North Korea gained custody of the funds, they began a careful money laundering process to cover up and cash out,” the researchers said. blender Cover up the trail.
The documented malicious activity involving nation-state actors took the form of cyber heists against foreign financial institutions, notably the 2015-2016 SWIFT bank cyber hack, and the most recent activity resulted in the deployment of a backdoor called AppleJeus that Backdoors masquerade as cryptocurrency exchanges to loot and transfer funds to their accounts.
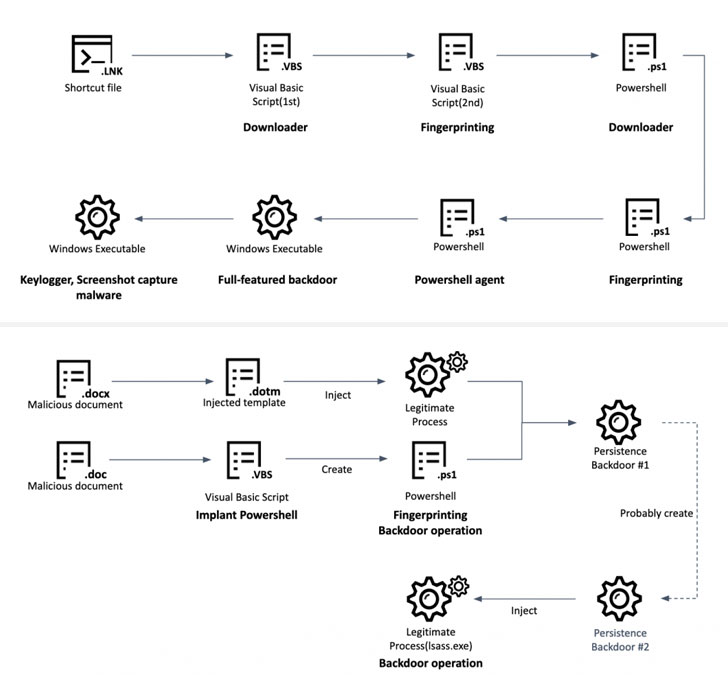
SnatchCrypto attacks are no different, as they orchestrate social engineering schemes to build trust with their targets by posing as legitimate VC firms, only to trick victims into opening malware-laden documents designed to run The payload of the malicious executable is received from a remote server over an encrypted channel.
Another method used to trigger the infection chain is to use a Windows shortcut file (“.LNK”) to get the next stage of the malware, a Visual Basic script, which then acts as a jumping point to execute a series of intermediate payloads that are installed Before a fully functional backdoor, the backdoor had “rich” capabilities to capture screenshots, log keystrokes, steal data from the Chrome browser, and execute arbitrary commands.
However, the ultimate goal of the attack is to monitor the financial transactions of infected users and steal cryptocurrencies. If a potential target uses a Chrome extension such as Metamask to manage a crypto wallet, the attacker would silently locally replace the main component of the extension with a fake version, alerting every time a large transfer is made to another account member.
To drain funds, malicious code injections are performed to intercept and modify transaction details as needed. “The attacker not only modified the recipient [wallet] addresses, but also pushes the amount of currency to its limit, essentially draining accounts in one go,” the researchers said. explain.
Erich Kron, a security awareness advocate, said: “Cryptocurrencies are a highly targeted area in cybercrime, due to the decentralized nature of money and unlike credit cards or bank transfers. Unlike a credit card or bank transfer, the transaction happens quickly and cannot be reversed in KnowBe4, it said in a statement.
“Nation-states, especially those subject to severe tariffs or other financial restrictions, can greatly benefit from stealing and manipulating cryptocurrencies. Many times a cryptocurrency wallet can contain multiple types of cryptocurrencies, making them a very Attractive target,” Kron added.





