Taiwanese company QNAP has warned customers to protect network-attached storage (NAS) devices and routers from a virus called dead bolt.
“DeadBolt has been broadly targeting all NAS exposed on the internet without any protection and encrypting user data for a bitcoin ransom,” the company said. Say. “QNAP urges all QNAP NAS users to […] Update QTS to the latest available version now. “
IoT search engine query Central system show at least 3,687 devices So far, encrypted by DeadBolt ransomware, most NAS devices are located in the US, Taiwan, France, Italy, UK, Hong Kong, Germany, Netherlands, Poland, and South Korea.
Additionally, QNAP urges users to check if their NAS devices are public facing, and if so, take steps to turn off the router’s port forwarding and disable Universal Plug and Play (Plug and Play) features of the QNAP NAS.
The consultation is beeping computer It was revealed that QNAP NAS devices were being encrypted by DeadBolt ransomware by exploiting a presumed zero-day vulnerability in the device software. The attack is believed to have started on January 25.
ransomware strains, which lock file Using the “.deadbolt” file extension, victims are asked to pay a ransom of 0.03 bitcoins (~$1,100) to a unique bitcoin address in exchange for a decryption key.
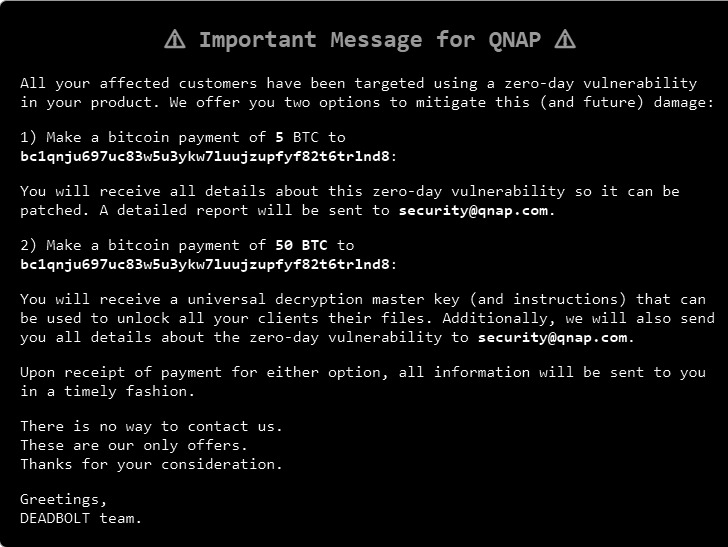
Most importantly, the operators of the ransomware claim If QNAP paid them 5 bitcoins (~$186,700), they were willing to provide full details of the so-called zero-day exploit. It is also preparing to sell a master decryption key that can be used to unlock files for all affected victims for an additional 45 bitcoins (~$1.7 million).
While it’s unclear if QNAP noticed the extortion demands, the company posted on Reddit, admit It silently forced an emergency firmware update to “increase protection against ransomware,” adding that “this was a tough decision. But we did it precisely because DeadBolt and we wanted to stop this attack as soon as possible.” “
QNAP devices have become common targets for ransomware groups and other criminals, prompting a flood of warnings from the company in recent months. January 7, suggestion Customers protect their NAS devices from ransomware and brute force attacks and ensure they are not exposed to the Internet.
When answered, QNAP indicates that the update was triggered as part of the QTS auto-update feature. “QNAP PSIRT leverages the ability to update QTS to protect against DeadBolt ransomware or other malware,” the company told Hacker News, adding that “the malware exploits one of the vulnerabilities fixed in this release. QSA-21-57. “
The company also said, vulnerability Related to a vulnerability affecting the QTS and QuTS hero operating systems, if successfully exploited, an attacker could run arbitrary code on an affected system. This issue has been resolved in the following releases –
- QTS 5.0.0.1891 build 20211221 and later
- QTS 4.5.4.1892 build 20211223 and later
- QuTS hero h5.0.0.1892 build 20211222 and later
- QuTScloud c5.0.0.1919 build 20220119 and later