Cybersecurity researchers have proposed a novel method that uses electromagnetic field emissions from Internet of Things (IoT) devices as a side channel to gather precise knowledge about different types of malware targeting embedded systems, even when obfuscation techniques are applied. The scene also hinders analysis.
With the rapid spread of IoT devices, it provides an attractive attack surface for threat actors, partly because they are equipped with higher processing power and can run a fully functional operating system. The latest research aims to improve malware Analyze to mitigate potential security risks.
The results of the research were presented by a group of scholars from the Institute of Computer Science and Random Systems (IRISA) at the annual Computer Security Applications Conference (ACSAC) Held last month.
“[Electromagnetic] The malware actually cannot detect the radiation measured from the device,” the researcher Say On a piece of paper. “Therefore, unlike dynamic software monitoring, malware evasion techniques cannot be applied directly. In addition, because malware cannot control the level of external hardware, it is impossible to turn off protection systems that rely on hardware functions, even if the malware has the maximum authority on the machine.”
The goal is to use side-channel information to detect abnormalities that deviate from previously observed patterns, and to issue alarms when suspicious behaviors of simulated malware are recorded compared to the normal state of the system.
Not only does this require no modification to the target device, the framework designed in the research can also detect and classify covert malware, such as kernel-level rootkits, ransomware, and distributed denial of service (DDoS) botnets, such as Mirai, to count invisible variants .

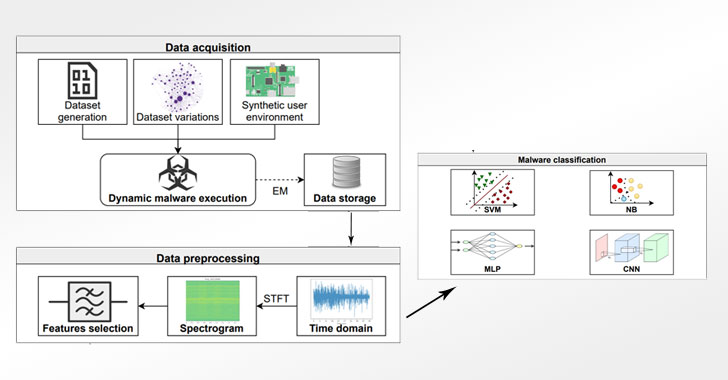
The side-channel approach is carried out in three stages, including measuring electromagnetic radiation while executing 30 different malware binaries and performing benign video, music, pictures, and camera-related activities to train convolutional neural networks.CNN) Model, used to classify real-world malware samples. Specifically, the framework takes executable files as input, and only relies on side-channel information to output its malware tags.
in a experimental device, The researchers chose Raspberry Pi 2B as the target device with a 900 MHz quad-core ARM Cortex A7 processor and 1 GB of memory. They used a combination of an oscilloscope and PA 303 BNC preamplifier to collect and amplify electromagnetic signals, effectively predicting three types of malware The accuracy rates of its related families are 99.82% and 99.61%, respectively.
“[B]y Using a simple neural network model, a large amount of information about the state of the monitored device can be obtained by only observing the state of the monitored device [electromagnetic] Dissemination,” the researchers concluded. “Our system is robust to various code conversions/obfuscations, including random garbage insertion, packaging, and virtualization, even if the system is not aware of this conversion before.