In December 2021, researchers discovered a new ransomware-as-a-service called ALPHV (aka “black cat“), believed to be the first professional cybercriminal group to create and use a strain of ransomware rust Programming language. In this post, we’ll explore some of the clues left by a developer who was allegedly hired to write code for a variant of the ransomware.
Image: Hero.
According to analysis Posted this week by Varonis, ALPHV is actively recruiting operators from several ransomware groups, including REvil, BlackMatter, and DarkSide, and offering affiliates up to 90% of the ransom paid by victimized groups.
“The group’s leak site has been active since early December 2021 and has named more than 20 victim groups as of late January 2022, but the total number of victims may be higher, including those who paid ransoms to avoid exposure,” Varoni’s Jason Hill wrote.
for more malware to move to rust It is considered a safer programming language compared to C and C++, writes katarin simpanu for record. The results of it? Security defenders have been looking for coding weaknesses in many ransomware, and if more people start turning to Rust, finding those weaknesses could become more difficult.
researchers in the future of records Said they believed the ALPHV/BlackCat authors had previously been involved in the notorious REvil ransomware cartel in some capacity. Earlier this month, the Russian government announced that it had arrested 14 individuals in Russia believed to be operators of REvil at the request of the United States.
Nonetheless, based on these actions, REvil continues Paul Roberts exist reverse lab“The recent arrests have not resulted in a noticeable change in the detection of REvil’s malicious files,” Roberts wrote. “In fact, the detection of files and other software modules related to the REvil ransomware increased slightly in the week following the arrest by Russia’s FSB intelligence agency.”
at the same time, US State Department have $10 million standing award Information used to identify or locate any individual holding a key leadership position at REvil.
Who is BIRS?
A confidential source recently spoke privately with a support representative who asked questions and inquiries on multiple cybercrime forums on behalf of a large and popular ransomware affiliate program. Affiliate representatives confirmed that the handle knows ALPHV’s encoder”Binns” on several Russian forums.
on the cybercrime forum slope, user Binrs says they are a Rust developer who has been coding for 6 years. “My stack is Rust, nodejs, php, golang,” Binrs said in an introductory post, claiming to be fluent in English.Binrs then sign the post with their ID number poison, a peer-to-peer instant messaging service.
a named “smiseoOn the Russian forum BHF, smiseo advertises “clipper” malware written in Rust that swaps the attacker’s bitcoin address when a victim copies a cryptocurrency address to their computer’s temporary clipboard.
nickname”YB cat” Advertise the same ToX ID on Carder[.]UK, the user claims ownership of the Telegram account @CookieDays, and said they could be hired for software and robotics development of “any level of complexity.” YBCat primarily sells “installers,” which allow paying customers to load malware of their choice on thousands of hacked computers simultaneously.
There is also an active user named Binrs on the Russian crime forum wwh-club[.]co who say they are Rust coders can be reached via the @CookieDays Telegram account.
On the Russian forum Lolzteam, the username “Dukeman” using the @CookieDays Telegram account in his signature. In one thread, DuckerMan promotes an affiliate program called CookieDays that lets people make money by getting others to install malware-infected cryptominers. In In another thread, DuckerMan is selling a different clipboard hijacker called Chloe Clipper.

CookieDays earning program.
According to threat intelligence firm Flash point, Telegram user DuckerMan used another alias – Sergey Duck. These accounts are most active on the Telegram channels “Bank Account Sales”, “Malware Developers Community” and the popular English-language cybercrime forum “Raidforums”.
i am duckman
This GitHub take one Sergey Darkman Lists dozens of code repositories that the user has posted online over the years. Most of these projects are written in Rust, while the rest use PHP, Golang, and Nodejs — the same coding languages Binrs specified on RAMP. The Sergey DuckerMan GitHub account also said it was linked to the “DuckerMan” account on Telegram.
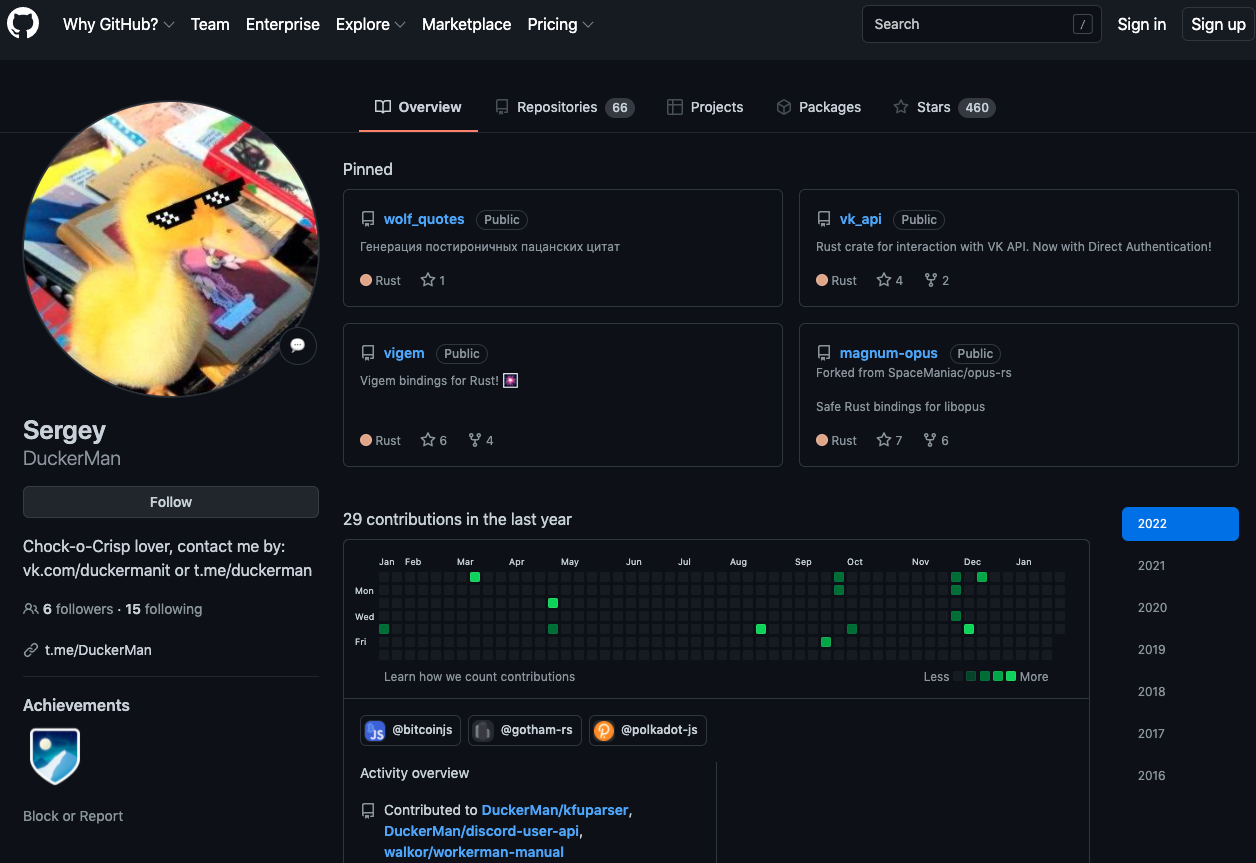
GitHub profile for Sergey DuckerMan.
Sergey DuckerMan has left many accolades for other programmers on GitHub – 460 to be exact.For example, DuckerMan gave one star in June 2020 A proof-of-concept ransomware strain written in Rust.
Sergey DuckerMan’s Github profile shows their social media accounts at Contact information (Russian version of Facebook/Meta) yes vk.com/duckermanit. The profile is limited to friends, but states that it belongs to Sergey Pechnikov from Russian Shua.
View the Duckermanit VKontakte configuration file at archive.org Shows that until recently it had a different name: Sergey Kryakov. The current profile picture on Pechnikov’s account shows a young man standing next to a young woman.
KrebsOnSecurity got in touch with Pechnikov with Russian transliteration via VKontakte’s built-in instant messaging feature.
“I’ve heard of ALPHV,” Pechnikov replied in English. “That sounds cool, and I’m glad Rust is becoming more popular, even in the malware space. But I don’t have any connection to ransomware at all.”
I set out to explain the clues that led to his VK account, and how key cybercriminals in the ransomware space identified Binrs as the core developer of the ALPHV ransomware.
“Binrs aren’t even programmers,” Pechnikov chimed in. “He/she can’t be a DuckerMan. I’m a DuckerMan.”
BK: right. Well, according to Flashpoint, Telegram user DuckerMan also uses the alias Sergey Duck.
Sergey: Yes, it’s me.
BK: So you can see how I got to your profile?
Sergey: Yes, you are a very good investigator.
BK: I noticed that this config file used to have a different name appended. A “Sergei Kryakov”.
Sergey: This is my old last name. But I hated it so much that I changed it.
BK: What do you mean Binrs aren’t even programmers?
Sergey: i didn’t find any [of] His accounts on sites like GitHub/stack overflow. I’m not sure, do binrs sell Rust Clipper?
BK: So you know his job! I think despite all this, you still don’t think you were involved in writing malware?
Sergey: Well, no, but I have some “connections” with these people. Speaking of Binns, I also started researching his character in October.
BK: interesting. What made you want to study his character? Also, please help me understand what you mean by “connected”.
Sergey: I think he’s actually a bunch of people. I telegraphed him from different accounts and he spoke differently. Maybe some of them are tied to ALPHV in some way. But on forums (I’ve only checked XSS and Exploit) he speaks the same way.
BK: …
Sergey: I don’t know how to explain it. By the way, binrs is really silent right now, I think he’s keeping a low profile. Well, that’s all I know.
No doubt he is. I love talking to Sergey, but I also have a hard time believing most of what he says. Also, it bothers me that Sergey doesn’t fully question the logic behind the thread that led to his VK account. In fact, he has said several times that he was impressed by the investigation.
In many previous breadcrumb stories, at this point, respondents often claimed they were set up or framed. But Sergey never even came up with the idea.
I asked Sergey how he would explain all these connections had he not been involved in writing the malware in some way. His answer, our final exchange, was again ambiguous.
“Well, I only have the code on github,” he replied. “So you can use [by] Anyone, but I don’t think my project is suitable for malware. “


