I recently jumped on Lookout Podcast Talk about virtual private networks (VPNs) and how they extend beyond the original use case of connecting remote laptops to the corporate network. Even in this new world where people use personal devices and cloud applications, VPNs remain the go-to solution for remote and cloud access. After talking with Hank Schless, I was inspired to put some additional thoughts on VPNs on paper.
When most organizations were forced to move to remote work last year, they needed a quick-fix solution that would allow remote employees to securely access work resources. For many, this solution comes in the form of a VPN. However, VPNs are not designed for bring-your-own-device (BYOD) and cloud application use cases.
While VPNs can provide remote access, their lack of security may come as a surprise. That’s because VPNs are built for only a small percentage of employees who want to work from home. They also put too much trust in the device and the user. But now, as work from anywhere continues, it’s important to rethink how to provide access to the entire organization in a secure way.
What are the challenges of a remote-first workforce?
When they debuted two decades ago, when laptops were becoming commonplace, VPNs were the de facto way to connect remote workers to an organization’s data center. Back then, computers were still connected using modems and services like iPass. VPNs run on top of services like iPass to create a “private network” and keep transfers secure.
But the technology landscape has changed dramatically since then. In several ways, they were built to solve yesterday’s problems.
The widespread adoption of cloud applications now means that the way we store and access work data is completely different. On any given day, I connect to internal development systems, access documents on Google Workspace, send Slack messages to colleagues, and use Zoom to attend meetings. I can do all of this with equal ease on my smartphone and laptop.
Many Lookout customers may have a similar experience, which also includes access to applications on AWS or Azure, such as SAP S/4HANA. When we work remotely, we’ve grown accustomed to having seamless access to what we need anytime, anywhere and working from whatever device we choose.
Another major challenge posed by this new environment is that organizations do not have the necessary visibility into their complex IT environment.
Unlike in the past where you could only use work-issued devices on a company-managed network, employees are accessing work resources using devices, networks, and software that your IT team may not control or even know about. This greatly increases your organization’s attack surface.
Why are VPNs not suitable for the modern work environment?
One of the biggest problems with VPNs is that they provide complete web access to anyone who connects. Not just the connected device, but everything on that device’s network is also accessible. So neither malware nor stolen accounts can stop them from moving laterally through your infrastructure and causing harm.
When it comes to user experience, VPNs also have a poor track record. When direct access to the cloud is available anywhere, expecting your employees to log in to the VPN first to access these cloud applications can create barriers to their workflow. Think of it as forcing someone to go from Boston to New York City via Los Angeles – inefficient. If you’ve ever experienced slow page load times or slow downloads while using a VPN, it’s most likely due to your traffic being forced to take inefficient routes.
What are the options?
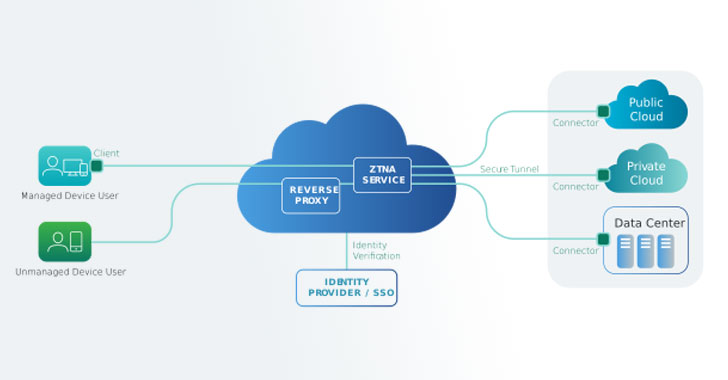
To address these new issues, and for the reasons above, a VPN doesn’t cut it in terms of giving your remote workers secure access to what they need. Secure access technologies such as Zero Trust Network Access (ZTNA) or Cloud Access Security Broker (CASB) follow where VPNs are broken.
These Secure Access Service Edge (SASE) technologies provide granular access to only the applications and data employees need, while continuously monitoring user and device behavior to dynamically adjust access based on risk. This means that the risk of lateral movement is greatly reduced, the connection between the user and the application is efficient, and the security of the connection goes far beyond encrypting the traffic between the two points.
ZTNA provides seamless connectivity to your applications without putting your data at risk
After all these years of connecting your employees to your organization, they deserve the credit they deserve. But the problem they were trying to solve at the time is no longer relevant. The challenge your organization now faces is giving your employees the freedom and flexibility to use applications in the cloud anywhere, while protecting your data. Moving from technologies like VPNs to next-generation alternatives like ZTNA is a good start.
learn How to boost your VPN Deploy and secure your organization with inspection Lookout Secure Access to Service Edge solution.
Note – This article was written and contributed by Sundaram Lakshmanan, CTO of SASE Products.