Getty Images
Over the past few months, as Russia has assembled tens of thousands of troops on the Ukrainian border and A subtle but far-reaching threat If Ukraine and NATO do not agree to the Kremlin’s demands.
A similar controversy is now playing out online, with unknown hackers taking down numerous Ukrainian government websites late last week and issuing cryptic warnings to Ukrainian citizens trying to receive services.
fear and expect the worst
“All data on the computer is damaged beyond recovery,” a message in Ukrainian, Russian and Polish appeared late last week on at least some of the infected systems. “All information about you has been made public, please fear and expect the worst.”
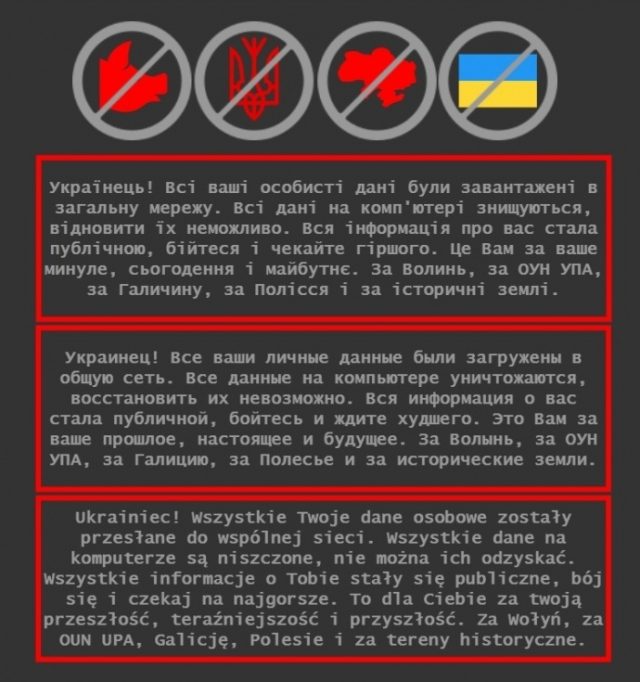
Around the same time, Microsoft wrote In a post over the weekend, “destructive” malware capable of permanently destroying computers and all data stored on them began to appear on the networks of dozens of government, nonprofit and information technology organizations in Ukraine. The malware — which Microsoft calls Whispergate — masqueraded as ransomware and demanded $10,000 in bitcoin to recover data.
But Whispergate lacked the means to distribute decryption keys and provide technical support to victims, traits found in nearly all working ransomware deployed in the wild. It also overwrites the Master Boot Record – the part of the hard drive that starts the operating system during boot.
“Overriding the MBR is atypical for cybercriminal ransomware,” members of Microsoft’s Threat Intelligence Center wrote in Saturday’s post. “In reality, the ransomware description is a ruse, and the malware corrupts the contents of the MBR and its target files. There are a number of reasons why this activity is inconsistent with the cybercriminal ransomware activity observed by MSTIC.”
Over the weekend, the deputy chairman of Ukraine’s National Security and Defense Council, Shershi Demedik, told the news outlet that preliminary results of a joint investigation of several Ukrainian state agencies indicated that a threat group called UNC1151 was likely behind the breach. black hand.The group is made up of researchers from the security firm Mandiant linked For the government of Belarus, an ally of Russia, it is behind an influence movement called Ghostwriter.
Ghostwriter steals victim credentials by using phishing emails and stealing domains to trick legitimate sites like Facebook. The authors of the Mandiant report wrote that, by taking control of content management systems belonging to news sites and other heavily traded properties, UNC1151 “mainly promotes anti-NATO narratives that appear to be aimed at weakening operations against Lithuania, Latvia and Poland. regional security cooperation”.
All evidence points to Russia
Ukrainian officials say UNC1151 likely represents Russia’s use of its skills to obtain credentials and infiltrate websites to disrupt Ukrainian government websites.in a statement, they write:
So far, we can say that all the evidence points to Russia being behind the cyberattack. Moscow continues to wage hybrid warfare and actively build power in information and cyberspace.
Russia’s cyber forces often work with the United States and Ukraine to try to use technology to change the political situation. The latest cyberattack is one manifestation of Russia’s hybrid war against Ukraine, which has been going on since 2014.
Its goal is not just to terrorize society. And destabilize the situation in Ukraine by halting public sector work and undermining Ukrainian confidence in the government. They can do this by planting false information into the information space about the vulnerability of critical information infrastructure and the “loss” of Ukrainians’ personal data.
damage assessment
There were no immediate reports that the defacements had a devastating effect on government networks, although Reuters on Monday report The Ukrainian cyber police found that last week’s defacement appeared to have destroyed “external sources of information.”
“Some external information resources were manually compromised by attackers,” police said, without elaborating. “It can already be said that the attack was more complex than modifying the website’s home page,” police added.
Microsoft, meanwhile, did not say whether the destructive data wiper it found on Ukrainian networks was only installed for possible later use, or if it was actually executed to wreak havoc.
There is no evidence that the Russian government was involved in the wiper malware or website sabotage, which Russian officials categorically deny. But given past events, Russia’s involvement is not surprising.
In 2017, a massive malware outbreak was initially thought to be ransomware Shut down computers around the world and lead to $10 billion in total losses, making it the most costly cyberattack ever.
not petya initially spread Via a legal update module of MEDoc, the widely used tax accounting application in Ukraine.Ukrainian and we Administration officials said Russia was behind the attack. In 2020, federal prosecutors charged four Russian nationals with hacking crimes involving NotPetya.



