In many ransomware attacks, the criminals who plunder the victim’s network are not the same as the crooks who initially gained access to the victim’s organization. More commonly, the compromised PCs or stolen VPN credentials the gang used to break in were purchased from cybercriminal middlemen known as initial access proxies. This article examines “Heze,” the hacker handle chosen by the main access brokers at cybercrime scenes in Russian.
Wazawaka has been an active member of several cybercrime forums over the past decade, but his favorite is the Russian-speaking community develop. Wazawaka’s early years on Exploit and other forums selling distributed denial of service (DDoS) attacks that can take websites offline for about $80 a day. But in recent years, Wazawaka has focused on peddling access to organizations and databases stolen from hacked companies.
In March 2020, Wazawaka wrote a post on Exploit: “Come on, loot, take the money!” In the post, he sold access to a Chinese company with more than $10 billion in annual revenue. “Let them see who’s the boss.”
According to their post on Exploit, Wazawaka works with at least two different ransomware affiliate programs, including lock bit. Wazawaka said LockBit had paid him roughly $500,000 in commissions in the six months ended September 2020.
Wazawaka also said that he and dark side, ransomware affiliate responsible for six-day outage Colonial pipeline Last year led to fuel shortages and price spikes across the country.This US State Department He has since offered a $5 million reward for information leading to the arrest and conviction of any DarkSide affiliate.
Wazawaka appears to take a uniquely communalist view that when the ransom-taken group refuses to cooperate or pay, any data stolen from victims should be posted on Russian cybercrime forums for all to loot — not sold privately to the highest bidder.thread after thread on crime forums cross-site scripting, the alias of Heze”uhodiran somwar“A link to a database download of companies that refused to negotiate five days after publication can be seen.
“The single and main principle of ransomware is: the information you steal should never be sold,” Uhodiransomwar wrote in August 2020. “If the ransom is not paid by one party, the community needs to receive it completely free. The information was stolen. “
Wazawaka wasn’t always so friendly to other online crooks. Over the past decade, his contact information has been used to register numerous phishing domains designed to steal credentials from people trying to transact on various darknet markets. In 2018, Wazawaka registered a series of domains posing as real domains. Hydra Darknet market. In 2014, Wazawaka revealed to another crime forum member via private message that he had made a lot of money stealing accounts from drug dealers in these markets.
“I once stole their QIWI account and it had up to $500,000 in it,” recalls Wazawaka. “The dealer would never go to the police and tell them he was selling something online and someone stole his money.”
Who is Heze?
Wazawaka used multiple email addresses and nicknames on several Russian crime forums, but the data collected by the cybersecurity firm Constellation Intelligence Shows that Wazawaka’s alter ego always uses one of three fairly unique passwords: 2k3x8x57, 2k3X8X57, and 00 virtual.
Over the years, Wazawaka has used all three passwords for one or all of his email addresses on crime forums, including wazawaka@yandex.ru, mixseo@mail.ru, mixseo@yandex.ru, mixfb@yandex.ru.
The last email address was used for registration about ten years ago Contact information (Russian version of Facebook) account Mikhail “mixed” Matveyev. The phone number associated with this Vkontakte account— 7617467845 — Specified by Russian phone provider Mega to residents Khakas, in the southwestern part of Eastern Siberia.
DomainTools.com [an advertiser on this site] Reports that mixfb@yandex.ru was used to register three domains between 2008 and 2010: ddosis.ru, best-stalker.com, and cs-arena.org. The last domain was originally registered in 2009 to Mikhail P. Matveyev, exist Abakan, Khakas.
Mikhail Matveev isn’t the most unusual name in Russia, but other clues help narrow it down.For example, early in his post to Exploit, Wazawaka can be seen telling members that he can be reached through an ICQ instant messaging account 902228.
An internet search for Wazawaka’s ICQ number found a 2009 account for Wazawaka on a now defunct discussion forum Kopiovo, a town of about 4,400 people in the Republic of Khakassia, Russia:
Mikhail’s mix
Also around 2009, someone started posting on Russian social media networks using the nickname Wazawaka and the 902228 ICQ address in an attempt to convince locals to frequent the site”fureha.ru,” it was advertised as another website catering to Khakassia residents.
According to the Russian Domain Observer 1stat.ru, fureha.ru registered to email address in January 2009 mix@devilart.net and phone number +79617467845, which is the same number bound to Mikhail “mixed” Matveyev Vkontakte account.
DomainTools.com says the mix@devilart.net address is used to register two domains: one named badamania[.]ru, there is also a TV Polka[.]ru. The phone number associated with this porn site registration in 2010 was 79235810401, also published by MegaFon in Khakassia.
search Skype Because the number suggests it was associated with the username “matveevatanya1” more than a decade ago.It was registered to a person who is now 29 years old Tatyana Matveyeva Driabina, Her Vkontakte profile shows that she currently lives in Krasnoyarsk, the largest city closest to Abakan and Abaza.
Tatyana seems likely to be a relative of Mikhail Matveyev, and possibly even his sister. Neither party responded to requests for comment. In 2009 Mikhail Matveev from Khakasabaza registered the username Wazawaka weblancer.net, a freelance exchange for Russian IT professionals. The Weblancer account states that Wazawaka is currently 33 years old.
In March 2019, Wazawaka explained his prolonged absence from Exploit and said he had a baby. “I’ll answer everyone in a week or two,” the crime actor wrote. “Being a dad – going on vacation for a few weeks.”
One of the many email addresses used by Wazawaka is devdelphi@yandex.ru, which was associated with an updated but deleted Vkontakte account of Mikhail Matveev and used the password 2k3X8X57. As usual, I put together a mind map showing the connections mentioned in this story:
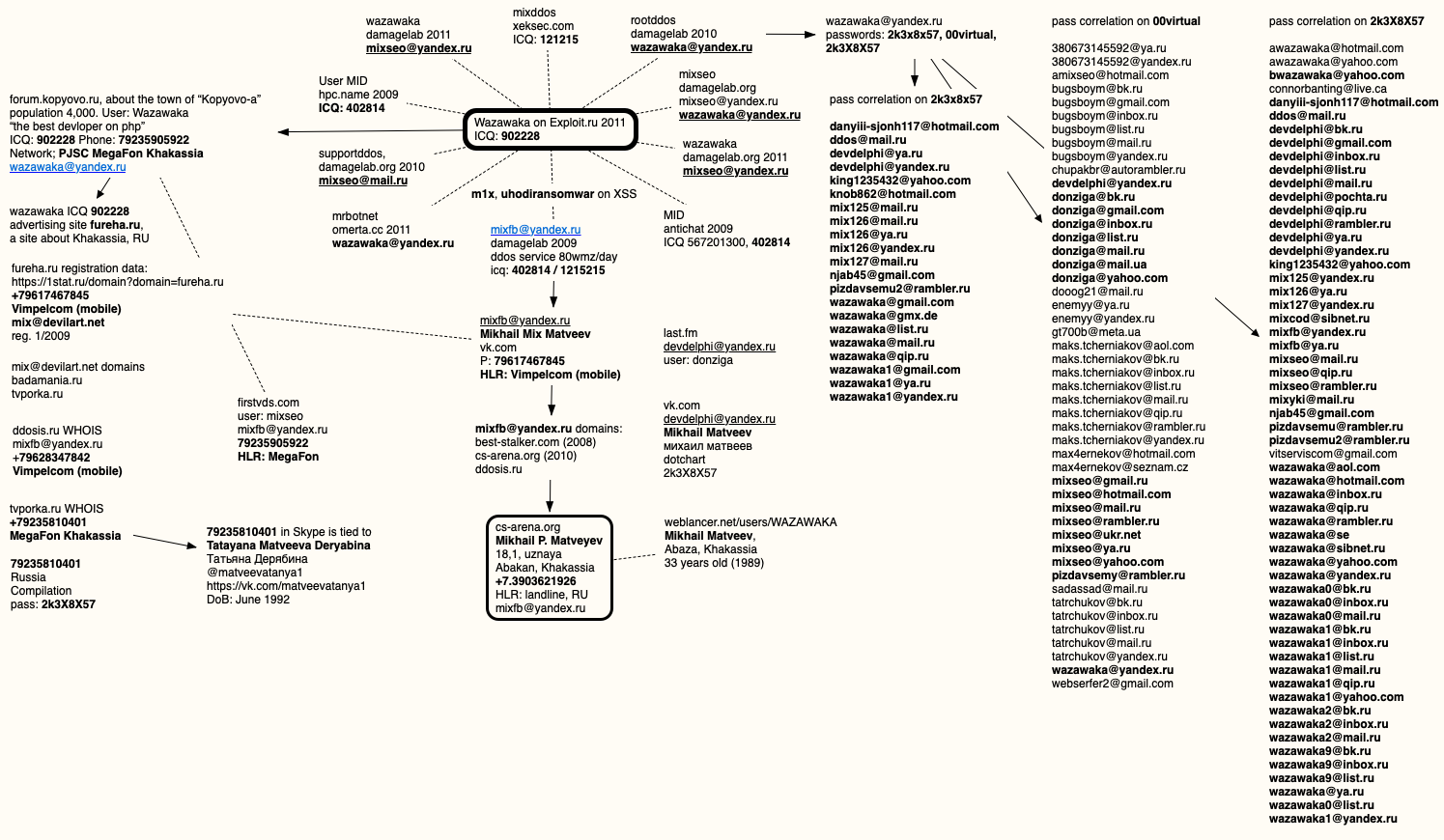
A rough mind map of the connections mentioned in this story.
Analyst at a Cyber Intelligence Company Flash point Said Wazawaka’s posts on various Russian crime forums that he is proficient in many areas of expertise, including botnet operations, keylogging malware, spam botnets, credential harvesting, Google Analytics manipulation, selling databases of spam operations, and launching DDoS attacks.
Flashpoint said Wazawaka/Mix/M1x likely shared cybercriminal identities and accounts with multiple other forum members, most of whom appear to be partners in his DDoS rental business a decade ago.For example, Flashpoint points to a Anti-chat In a 2009 forum thread, members claimed that M1x worked with a hacker nicknamed “Vedd” to develop his DDoS service, who was also said to be a resident of Abakan.
keep it real, mother russian will help you
Of course, all of this is academic, provided Mr. Wazawaka chooses to a) never leave Russia and b) avoid cybercriminal activity against Russian citizens. In a January 2021 post on Exploit about the arrest and subsequent demise of an affiliate of the NetWalker ransomware program, Wazawaka appears to have dropped those restrictions.
“Don’t shit where you live, travel locally, don’t go abroad,” Wazawaka said of his own personal mantra.
This may explain why Wazawaka is so lazy to hide and protect his cybercriminal identity: Incredibly, Wazawaka’s alter ego on the forum XSS – Uhodiransomware – Still using the same password he used for his Vkontakte account 10 years ago on the forums. Fortunately, XSS also requires a one-time code for his mobile authentication app.
The second step is to log in to Wazawaka’s account on XSS (Uhodiransomwar).
Wazawaka said NetWalker’s shutdown was the result of its administrators (aka “Bugatti”) becoming greedy, and then he went on to preach the need to periodically reinvent cybercriminal identities.
“I have some business dealings with Bugatti,” Wazawaka said. “This guy is too rich and started recruiting Americans as partners. What happens now is the result. But that’s okay. I hope Bugatti does some rebranding and starts from scratch  As for the seized servers, they should be hosting theirs in Russia Admin panel to avoid having their servers seized by Interpol, the FBI or whatever.”
As for the seized servers, they should be hosting theirs in Russia Admin panel to avoid having their servers seized by Interpol, the FBI or whatever.”
“Mother Russia will help you,” concludes Wazawaka. “Love your country and you’ll get away with it forever.”
If you liked this article, you might also like Who is Web Access Proxy “Babam”?


